Are you using a computer in your school or workspace with a firewall and limits which websites you can visit? Check out today’s list of the best ways to bypass it.
Firewalls have been around for as long as the internet. It’s a piece of software that works as a filter and monitors the inbound and outbound traffic of the machine. The main goal of the firewall is primarily to prevent attacks and keep your computer safe and sound.
While the firewall was primarily used for these things in the past, it poses a different problem today. On the one hand, it can protect your computer, but on the other hand, someone else can make restrictions to the outbound traffic.
This is something that is mainly found in schools or companies, where the administrator can make restrictions. People using these computers won’t be able to access the websites that are on the “blocked” list. Once the URL gets added to the list, any attempt to access a particular website will be rejected.
The users set up on a school or workplace computer rarely have administrative privileges. It means that you won’t be able to make changes to the firewall settings and remove a website from the list.
On the other hand, the firewall list may be set up on the router, meaning that regardless of what you do, you will have restrictions as long as you’re connected to the network. This also means that the same rules will apply even if you try with a different device.
People see this as a problem, but the good news is that there are solutions to this, and I’ll talk about them in today’s article.
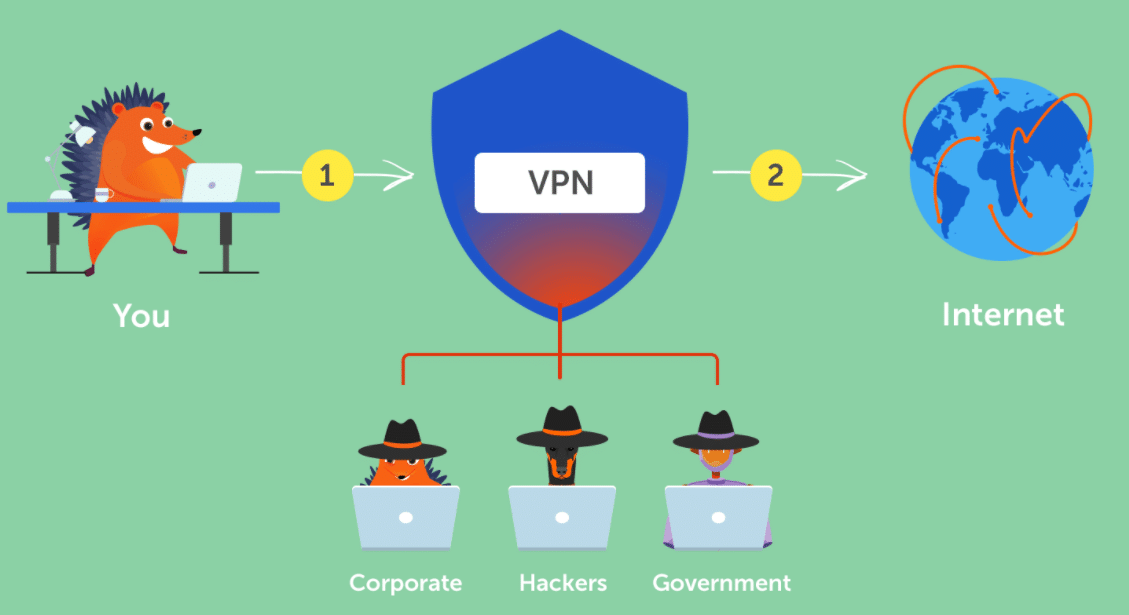
1. VPN
Credit to Namecheap
A VPN is a virtual private network that provides a secure and encrypted connection over the internet. This is done by connecting to a server run by the service provider. Its main task is to help you hide your real IP address and allow you to access restricted content and websites.
VPNs are nodes on other machines connected to the internet, acting as an intermediary that routes the traffic to the intended destination. A slight advantage a VPN has, in this case, is that it creates an encrypted tunnel where the data flows. As a result, if the traffic gets intercepted, it won’t be usable to anyone, making them a more secure option.
For bypassing a firewall’s restriction, the workings are identical. Instead of sending the data directly to the intended website server, the VPN routes it, fooling the firewall that the destination is different. Doing this would enable you to get access to websites that would otherwise be restricted.
Like in the proxy world, VPN services are available in abundance, giving you plenty of flexibility in choosing one. You have services like NordVPN, ExpressVPN, Surfshark, IPVanish, PIA, PureVPN, and so on.
Unlike with the proxies, going for a VPN means that you’ll need to download the service and activate it. Depending on the provider, you also have the option to use it through a browser extension, limiting the usage only to websites and not other applications on your computer.
Since all VPN services are paid, there is a free option that works up to a point. The Opera browser comes with a built-in VPN which is not a bad option to try if this is a good solution for you.
2. Proxy Server

I’ve talked about proxies quite a lot on this website, and here they are again. The idea behind using proxies is straightforward, and the principle is the same as if you’d want to use them to hide your IP address.
Depending on the type of proxy, a proxy server or node is a machine that you “connect” to and route all your traffic through there. It acts as a middleman between your device and the website you want to access.
Without a proxy, your computer will send out request packages to a website which will need to pass through the firewall. In these cases, the firewall will see the request and block it, which is where a proxy comes into play.
Since the traffic gets routed through a proxy, the firewall will see it going to some IP address that doesn’t match the ones in the list of blocked sites. As a result, it won’t intervene, and you’ll have full access to the website.
There are tons of proxy options for you to choose from and with different price options that would fit anyone’s pocket. On top of that, there are also 3 types of proxies to choose from, so the possibilities are endless.
Among the many options are Bright Data, Soax, Proxy-Cheap, Proxy-Seller, Smartproxy, Stormproxies, BlazingSEO, InstantProxies, and many more.
All of these offer datacenter, residential and mobile proxies at different prices, so choose the one that fits your needs and budget.
One thing to keep in mind is that you’ll need to set up the proxy on your browser or computer settings to use it.
3. Tor Browser

While I’m on the subject of browsers, there is a dedicated browser designed for anonymity and privacy. The Onion Router is a popular option for people who want to hide their identity online or bypass restrictions, meaning that it would be a good option.
Tor is a project that relies on volunteers to keep the network running and provide nodes. These nodes work similarly to proxies or VPNs and help bounce around the traffic throughout the globe. If I’m honest, this is a bit of an overkill for bypassing a firewall, but it is a potential approach, so here it is.
The primary goal is to provide anonymity and that it does well. Once the packets leave your computer, they get redirected to the nodes and then end up at the website’s server. Like in the previous two cases, the firewall won’t know that you’re trying to access a restricted website, so it won’t prevent you from that.
Going for this approach means that you won’t have to pay for a service, which is a nice touch. To get started, you’d need to download the installer, install the browser and run it. There is an initial setup process that takes a bit longer, but it won’t have any issues after that.
One thing to note is that Tor is designed for maximum anonymity, something you take advantage of. With that said, you won’t need everything to get past the firewall restrictions.
4. Use a different connection

This seems like an obvious option, but sometimes people seem to neglect it. Let’s say that the firewall is on the Ethernet or your router, meaning that any device connected to the network will have the same set of limitations. The solution is to connect to a different network, which may seem simple, but it’s not always.
Wherever we go, we’re surrounded by wireless networks, which is good, meaning that we have a lot to choose from. The problem is that they are almost always password-protected, and if you don’t know the password, you won’t be able to connect to it. The solution to this problem is in your pocket.
There isn’t a single person in the world that doesn’t have a smartphone, meaning that you have the crucial feature for this – hotspot.
You use your phone as a WiFi router to connect to it and browse the internet. Using a hotspot means that you will need an active data plan, which most do, so I would still advise you to double-check this despite not being a problem.
The procedure is relatively simple, and you can find guides for your phone. Once you’re connected to the WiFi from your phone, there won’t be any firewall that will limit your access.
Alternatively, you can use the tethering option and connect your phone to your computer via a USB cable. This is a good way if you don’t want anyone to see your wireless network.
5. Remote access

This one may sound weird, but hear me out. If you’re at work or school, you may have restrictions, but your home computer doesn’t, so you can use it to get access to blocked websites.
Remote access is often used for troubleshooting where someone accesses a computer over the internet and controls it as it was in front of him. While that is a primary goal, you can use it to access restricted websites.
If you try to connect remotely to your home computer, the firewall will see it as a connection to a website that isn’t on the list of blocked ones. Since you are only streaming and controlling your computer, none of the packets sent to your home computer will be seen by the firewall, so you’ll have no issues.
There is one thing to keep in mind, though. Remote connection requires your computer to be on even when you’re not home, so it’s a helpful tip if you ever need to use this.
6. Use the website’s IP address

The last way I’ll talk about is to use an IP address instead of the URL. Before you get too excited, there is something you should know.
Some firewalls work on a URL basis and just block access based on that, while others do for the IP. When you type in a URL, the DNS finds the IP address associated with it and pushes the data there.
Since this is a freeway, you can test it out before you start to lean on it. Navigate to a DNS lookup website and paste the URL you want to access.
This will give you an IP address which you should paste in the address bar. If you get access to the website, you’re good to go; if not, you’ll need to use another method.
7. Proxy Site

You may be confused about this, considering I already mentioned proxies in the second section. Proxy sites offer similar results with a bit less effort.
Proxy sites are websites where you paste the URL you want to access, and the proxy website does the rest. It will redirect the traffic through some proxy somewhere in the world, and you’ll have no restrictions.
The firewall won’t intervene because it will see a URL or IP address that isn’t part of the list of blocked sites.
At first glance, it seems like the perfect option, but it’s not the best one. You have no information about the proxies used, meaning that it’s not the most secure way for some more sensitive work. For plain old browsing, you should be fine, though.
FAQ
Q. Is it legal to bypass a firewall?
Yes, as far as the law goes, you won’t have any issues if you decide to bypass the firewall. Once you bypass the firewall, what you do is crucial, and malicious activities are usually against the law.
With that said, if someone from your school or company finds out, there may be some consequences.
Q. Can I use free proxies to bypass a firewall?
Technically you can. Free proxies are like the paid ones, and you will use them to reroute your traffic, meaning that as far as bypassing the firewall, you’ll be fine.
The problem with using free proxies is that you don’t know who manages them, and in cases where you may need to enter some sensitive data, things may be problematic. A third party may use that data, leading to additional problems.
Q. What is the best method for bypassing a firewall?
There isn’t the best or worst; there is the one that suits you the best. People on a budget may go for the Tor or Opera option, while others may pay for a service like a proxy or a VPN.
Q. Can I disable the firewall altogether?
If you have administrative privileges or access to the router, you can disable the firewall, but I wouldn’t recommend that. Disabling that feature leaves you vulnerable to outside attacks, something the firewall is there to prevent.
Q. How to find which websites are blocked by the firewall?
There are two options here – you can find the list or not. If you have an administrative account or access to the router, you can find the list. This involves opening the firewall settings on your computer or logging in to the router.
Within the settings, you will find the list, and you may even have access to modify it. On the other hand, if you aren’t an admin user or cannot access the router’s dashboard, you have no way to find out which websites are blocked.
Conclusion
Firewalls are tools that have two sides, a good and a bad one. On the positive side, you have a digital wall protecting you from outsiders. On the other hand, someone may use it to limit your access to the internet.
To avoid that, I’ve outlined several methods that you can use to grant you full access. Keep in mind that for some you’ll need to pay, while others require some work.
